Here you can download file MobaLiveUSB_0.2. 2shared gives you an excellent opportunity to store your files here and share them with others. Join our community just now to flow with the file MobaLiveUSB_0.2 and make our shared file collection even more complete and exciting. Download 'PUH edition v2' torrent (Software » PC). Download millions of torrents with TV series, movies, music, PC/Playstation/Wii/Xbox games and more at Bitsnoop. You can get a µTorrent compatible list here. 1 Verify as a good torrent (0). MobaLiveUSB; Moba Live. Is this file safe? Check the directory. Should I ignore Zalman users and use /E2B, or use /_ISO and not worry about people trying to follow Tuts #30 and 43, etc.??? ===== Test your bootable USB Flash Drive IN qemu ===== 1.Make your Easy2boot flash dive. 2.Download MobaLiveUSB_0.2.exe from link below: 2.Copy MobaLiveUSB_0.2.exe in root of your bootable usb flash drive. Mobaliveusb 0 2 exe download free. Download mobaliveusb exe free shared files. [EXE] Xbox Live Bio Art Creator by o TRiPPiNz V3.1.0.rar from all world's most popular shared hosts. So i thought it may be helpful for some users too and now do as below: ===== 1.Make your bootable flash dive. 2.Download MobaLiveUSB_0.2.exe from link below: 2.Copy MobaLiveUSB_0.2.exe in root of your bootable usb flash drive. 3.Run MobaLiveUSB_0.2.exe inside your flash drive That's all,After few seconds your bootable flash drive will be run in.
CoWPAtty - Brute-force dictionary attack against WPA-PSK. Copyright(c) 2004-2018 Joshua Wright -------------------------------------------------------------------------------- INTRO Right off the bat, this code isn't very useful. The PBKDF2 function makes 4096 SHA-1 passes for each passphrase, which takes quite a bit of time. On my Pentium II development system, I'm getting ~4 passphrases/second. The SHA-1 code I'm using has been optimized to the best of my ability (which isn't saying that much), but I doubt if it would be possible to optimize it such that the tool experiences an exponential performance increase.
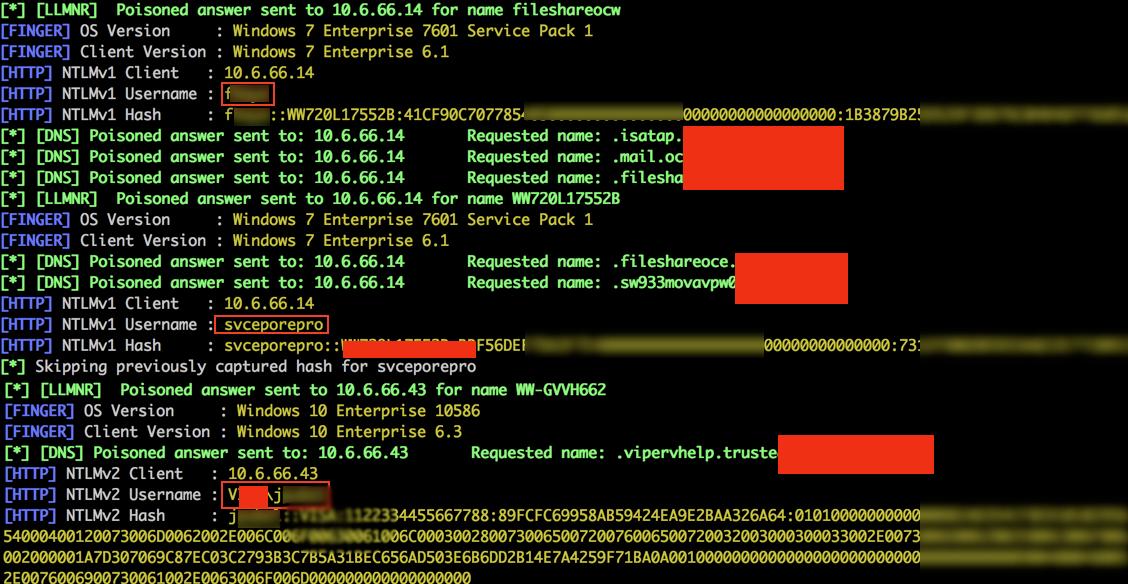
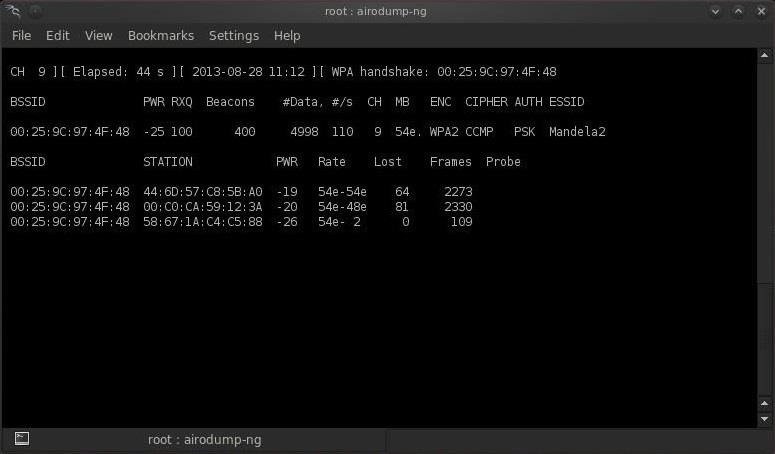
However, if you are auditing WPA-PSK or WPA2-PSK networks, you can use this tool to identify weak passphrases that were used to generate the PMK. Supply a libpcap capture file that includes the 4-way handshake, a dictionary file of passphrases to guess with, and the SSID for the network: $./cowpatty -r eap-test.dump -f dict -s somethingclever cowpatty 4.0 - WPA-PSK dictionary attack.
Cowpatty 4.8 - WPA-PSK dictionary attack. Collected all necessary data to mount crack against WPA2/PSK passphrase. Starting dictionary attack. Please be patient. The PSK is '12345678'. Torrent crack for en route 2017. 5 passphrases tested in 0.00 seconds: 50000.00 passphrases/second. Apr 18, 2012 Everyone who has a wireless network and some basic computer knowledge might be interested in the free product presented here, called coWPAtty for Windows. With coWPAtty for Windows you will be able to decypher WiFi keys for protected networks with WPA and WPA2-PSK.
Collected all necessary data to mount crack against WPA/PSK passphrase. Starting dictionary attack. Please be patient. The PSK is 'family movie night'. 4087 passphrases tested in 59.05 seconds: 69.22 passphrases/second $ The files 'dict' and 'eap-test.dump' are included with this distribution for testing purposes. If your SSID has spaces or other non-ASCII characters, enclose it in quotes so the shell doesn't interpret it as multiple parameters.
This tool can also accept dictionary words from STDIN, allowing us to utilize a tool such as John the Ripper to create lots of word permutations from a dictionary file: $ john -wordfile:dictfile -rules -session:johnrestore.dat -stdout:63 cowpatty -r eap-test.dump -f - -s somethingclever In the default configuration of John the Ripper, common permutations of dictionary words will be sent as potential passwords to coWPAtty. For example, here is a list of the words John will create from the input word 'password': jwright@mercury:~$ echo password >word jwright@mercury:~$ john -session:/tmp/delme -wordfile:word -rules -stdout password Password passwords password1 Password1 drowssap 1password PASSWORD password2 password! Password3 password7 password9 password5 password4 password8 password6 password0 password. Psswrd drowssaP Drowssap passworD 2password 4password Password2 Password! Password3 Password9 Password5 Password7 Password4 Password6 Password8 Password. Password0 3password 7password 9password 5password 6password 8password Passwords passworded passwording Passworded Passwording words: 49 time: 0:00:00:00 100% w/s: 49.00 current: Passwording jwright@mercury:~$ John the Ripper is available at. Note that it is also possible to mount a precomputed attack against the PSK.
Recent Pages
- Tamil Devotional Songs Vinayagar Agaval Lyrics
- Subtitle Translation Wizard 42 Crack
- Patch Navitel Comexe
- Zuliya Radzhabova Kniga Doroga K Sebe 9 Stupenej
- Download Free Write Ways Lesley Wing Jan Pdf
- Spisok Perepisi Naseleniya Drevnej Rusi V Epohu Ivana Groznogo
- Free Download Soniye Hiriye Video Song Shael
- Windows Xp Sp3 Rus Ustanovochnij Zverj S Drajverami Programmi
- Kirgizcha Tush Zhoru Kitep
- Driver Joystick Usb Welcome
- As400 Tutorial For Beginners Pdf Free